What are the best practices for implementing DevSecOps
Implementing DevSecOps is vital for organizations looking to enhance security while maintaining fast and flexible software development. By integrating security throughout the development process, teams can proactively address risks and ensure that everyone shares responsibility for software safety. This guide will highlight key practices to help organizations successfully adopt DevSecOps principles, improving both security and efficiency.
Shift Left
The "Shift Left" approach emphasizes integrating security practices early in the software development lifecycle, which involves addressing security vulnerabilities as the code is being written, rather than waiting until later testing phases.
This proactive stance helps to minimize the cost and complexity associated with fixing issues at later stages, as it enables developers to catch potential flaws early on.
.png)
Example: Netflix uses static analysis tools that catch security flaws at the coding phase, saving significant resources and lowering production issues.
Automate Security Testing
Automating security testing involves using tools to conduct vulnerability scanning, code analysis, and compliance checks consistently across the CI/CD pipeline.
This practice ensures that security checks are applied uniformly and frequently, which accelerates the detection of threats and simplifies the remediation process.
Automation not only improves efficiency but also reduces human error in security assessments.
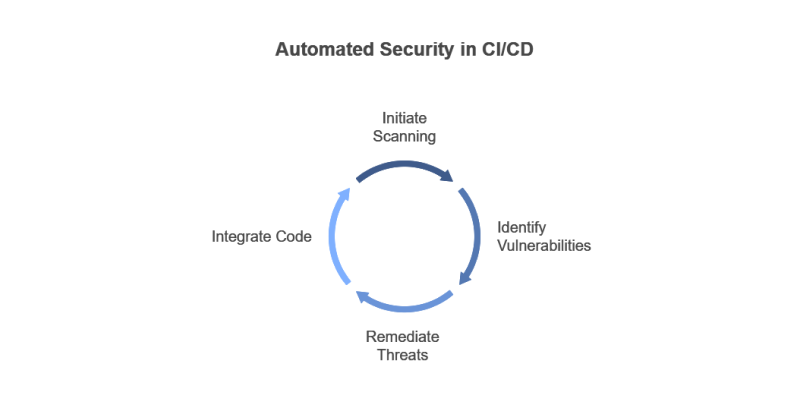
Example: Tools like Snyk and SonarQube automate the scanning of dependencies to identify vulnerabilities in real time during code integration, helping to prevent issues from reaching production.
Continuous Integration (CI) and Continuous Delivery (CD)
CI/CD is a set of practices enabling teams to release software updates more frequently and reliably.
By embedding security checks within CI/CD pipelines, organizations can ensure that security assessments are conducted at every deployment stage, allowing teams to integrate security seamlessly into their development workflows without introducing delays.
This continuous assessment helps maintain a high-security standard throughout the software lifecycle.
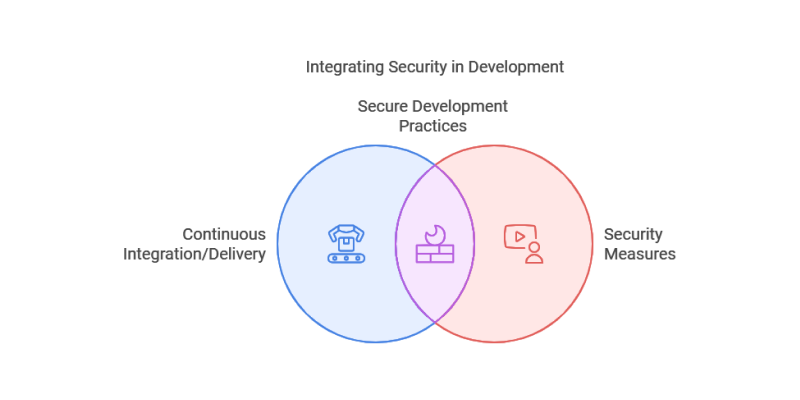
Example: Etsy enforces security standards by incorporating automated security tests into their CI/CD pipeline, preventing insecure code from being deployed.
Threat Modeling
Threat modeling is a structured process that identifies and evaluates potential security threats and vulnerabilities during the design phase of software development.
By anticipating security risks early, teams can implement appropriate measures to mitigate these threats proactively, rather than responding reactively after issues arise.
This method enhances the overall security of the software product from the outset.
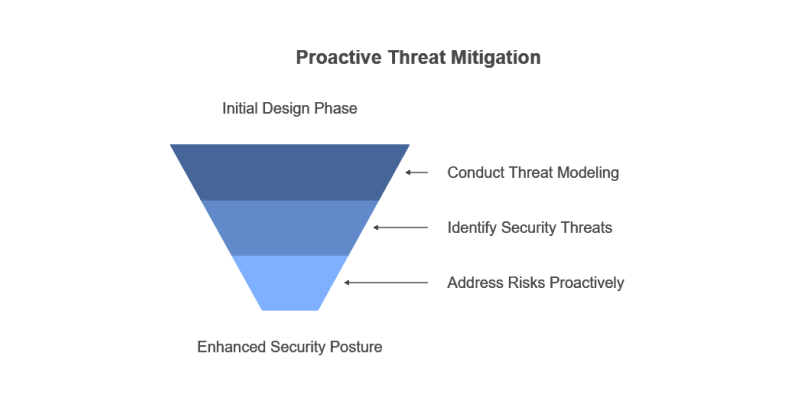
Example: Microsoft integrates threat modeling as a mandatory step in their Security Development Lifecycle (SDL), which allows developers to foresee and address security risks early in the development process.
Role-Based Access Control (RBAC)
It is a security measure that restricts user access to information and systems based on their organizational role.
By ensuring that users only have the permissions necessary for their tasks, RBAC minimizes the risk of insider threats and unauthorized access to sensitive data.
This practice is particularly crucial in sectors that handle confidential information.
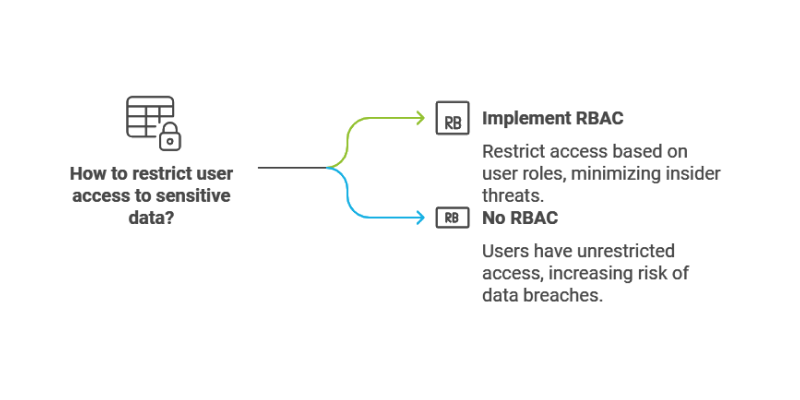
Example: Financial institutions implement RBAC to limit access to sensitive data, ensuring that only authorized personnel can view or manipulate this information, thereby enhancing internal security.
Secure Coding Standards
Establishing secure coding standards involves creating and enforcing guidelines that prevent common security vulnerabilities, such as SQL injection and cross-site scripting.
These standards serve as a foundation for developers to follow, ensuring that secure coding practices are consistently applied throughout the development process.
Regular training on these standards helps reinforce their importance among development teams.
Example: Google utilizes a standardized secure coding framework to train developers, emphasizing best practices that help reduce errors and enhance the overall security of applications.
Immutable Infrastructure
Immutable infrastructure refers to a model where components are never modified after deployment. Instead, if changes are needed, the infrastructure is rebuilt and redeployed in a secure state.
This approach prevents the introduction of vulnerabilities that might occur through untracked changes and ensures that the infrastructure is always in a known, secure configuration.
Example: Many organizations use container orchestration platforms like Kubernetes to create immutable infrastructures, allowing applications to be redeployed securely and consistently without lingering vulnerabilities.
Cloud-Native and Container Security
As organizations increasingly adopt cloud-native and containerized architectures, securing these environments becomes crucial.
This involves implementing measures like container runtime protection, configuration checks, and regular vulnerability scanning to protect against potential supply chain attacks.
Ensuring that both the applications and their underlying infrastructure are secure is key to maintaining a strong security posture.
Example: Spotify employs container runtime protection to secure its microservices, allowing teams to swiftly identify and remediate vulnerabilities specific to their containerized applications.
Policy as Code
Policy as Code involves defining security policies in a machine-readable format that can be automatically enforced across infrastructure and applications.
This practice promotes consistency in security standards and simplifies audits, as policies are integrated into the code and workflows.
It allows organizations to scale security measures efficiently without manual oversight.
Example: HashiCorp uses policy-as-code tools like Sentinel to programmatically enforce security policies across cloud infrastructure, ensuring compliance and consistency.
Enhanced Security Observability
Enhanced security observability refers to the use of monitoring tools that provide real-time visibility into the security status of applications and infrastructure.
This capability enables teams to quickly detect and respond to threats or anomalies, thereby improving the overall security posture.
Continuous monitoring helps identify potential issues before they can be exploited.
Example: LinkedIn implements observability tools that monitor application security, providing insights that enable teams to act swiftly against emerging risks.
Access Control and Obfuscation
Access control involves setting permissions to restrict access to sensitive data, while obfuscation techniques protect that data from unauthorized users.
Together, these practices safeguard critical information, such as API keys, from exposure and misuse.
Implementing fine-grained access controls ensures that only authorized users can interact with sensitive components.
Example: Cloud platforms like AWS and Azure provide tools for granular access control and data obfuscation, reducing the risk of unauthorized access and protecting customer data.
Incident Response and Bug Bounties
Strengthening incident response capabilities includes conducting regular drills and establishing processes for effectively managing security incidents.
Implementing bug bounty programs incentivizes external security researchers to discover and report vulnerabilities, creating an additional layer of security oversight.
This proactive approach helps organizations be better prepared for real-world attacks.
Example: GitHub conducts bug bounty programs and runs incident response simulations regularly to improve their preparedness for potential security incidents.
Educate Developers on Security
Providing ongoing security training for developers ensures they are aware of secure coding practices, potential vulnerabilities, and the principles of DevSecOps.
This education empowers developers to proactively prevent coding errors that could lead to security issues.
A well-informed development team is a critical line of defense against security threats.
Example: Microsoft mandates security training for its developers, emphasizing the importance of secure coding from the beginning of the development lifecycle.
Documentation and Compliance Reporting
Maintaining thorough documentation of security practices and generating compliance reports is essential for meeting regulatory requirements and facilitating audits.
Clear documentation helps ensure that all security measures are traceable, verifiable, and consistently applied throughout the development process.
This practice reduces regulatory risks and enhances transparency.
Example: Financial services firms, which face strict regulatory oversight, maintain detailed compliance reports for every stage of development, making audits more straightforward and reducing the risk of non-compliance.
Conclusion
Here we explores essential best practices for implementing DevSecOps, emphasizing the integration of security throughout the software development lifecycle. By adopting strategies such as "Shift Left," automating security testing, and enhancing collaboration among teams, organizations can proactively address vulnerabilities, improve their security posture, and maintain agility in their development processes.
These practices not only foster a culture of security awareness but also streamline compliance and incident response efforts, ultimately leading to more resilient applications.