Hypervisor Security in Cloud Computing: What You Need to Know

In cloud computing, a hypervisor plays a crucial role. It enables virtualization, allowing multiple virtual machines (VMs) to run on a single physical server.
The hypervisor manages resources like CPU, memory, and storage, ensuring that each VM operates independently.
However, since hypervisors control these VMs, they must be kept secure to prevent potential attacks that can affect the entire system.
What is a cloud hypervisor?
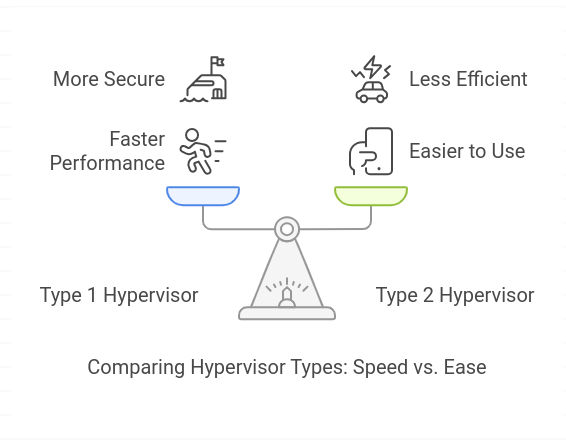
A cloud hypervisor is a software that allows virtual machines (VMs) to run on a physical server. It sits between the hardware and the operating system (OS), allocating resources to each VM and keeping them isolated. There are two main types of hypervisors:
Type 1 Hypervisor (Bare-metal)
A Type 1 hypervisor runs directly on the physical hardware without needing an operating system.
This makes it faster and more secure because it has direct access to the hardware and doesn't rely on an underlying OS. Since it operates at a lower level, there is less chance for security vulnerabilities associated with additional layers of software. Type 1 hypervisors are often used in enterprise environments and cloud infrastructure because of their high performance, efficiency, and security.
Advantages
- Performance: No intermediary OS, leading to higher resource allocation efficiency.
- Security: Fewer layers to exploit, and it isolates VMs better from the host system.
- Stability: Type 1 hypervisors are typically more stable for heavy workloads.
Disadvantages
- Complexity: They are harder to manage and may require more technical expertise.
- Hardware dependency: They often require specific hardware compatibility for full functionality.
Type 2 Hypervisor (Hosted)
A Type 2 hypervisor runs on top of an operating system, making it easier to use but less efficient and secure compared to a Type 1 hypervisor. Since it depends on the host operating system for resource management, it can introduce additional overhead, making it less suitable for high-performance environments or large-scale cloud deployments. Type 2 hypervisors are typically used for personal or development environments, where ease of use and accessibility are more important than raw performance or security.
Advantages
- Ease of Use: Since it runs on an existing OS, installation and configuration are more straightforward.
- Flexibility: It allows users to run different OSes on a single machine for testing or development without complex setup.
- Lower Cost: Often free or less expensive than Type 1 solutions, making them suitable for non-enterprise use.
Disadvantages
- Performance Overhead: Since it relies on the host OS, it can be slower and less efficient, especially under heavy workloads.
- Security Risks: The host OS adds another layer of complexity, and vulnerabilities in the OS can potentially be exploited to affect the hypervisor.
- Limited Scalability: Not suitable for enterprise-scale virtualization environments or high-performance applications.
In cloud computing, Type 1 hypervisors are commonly used because they offer better performance and security.
Why is Hypervisor Security Important?
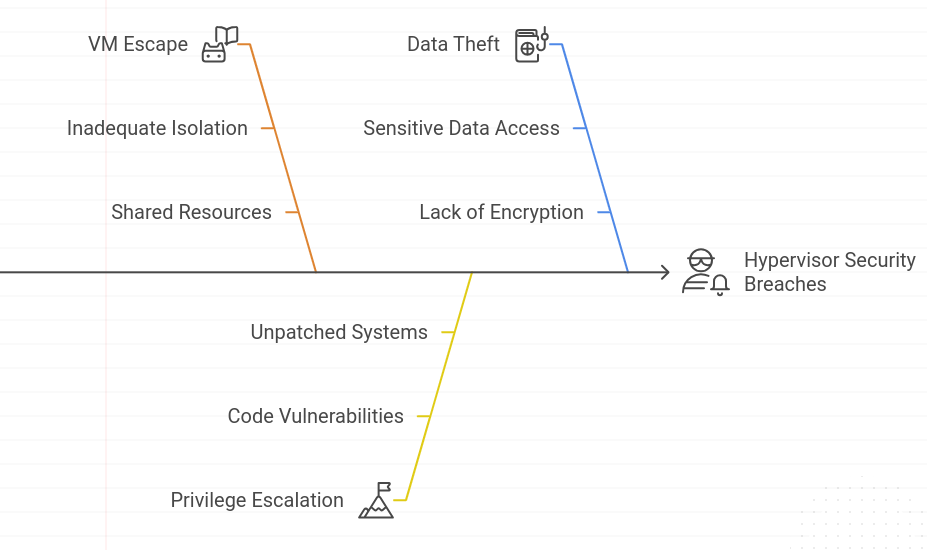
Hypervisors manage VMs, which often hold sensitive data and applications. If attackers take control of a hypervisor, they could potentially access multiple VMs at once, leading to serious risks such as:
VM Escape: If an attacker gains control of one VM, they might break out and access other VMs or the hypervisor itself.
Example: Imagine an attacker compromises a VM running on a cloud server. If the VM isn't properly isolated, the attacker could escape its boundaries and access other VMs on the same server, stealing sensitive data.
Privilege Escalation: Attackers can exploit weaknesses in the hypervisor to gain higher levels of access and control.
Example: If a vulnerability in the hypervisor’s code is discovered, attackers could escalate their privileges, taking control of the entire system and compromising all VMs.
Data Theft: If attackers breach the hypervisor, they could steal sensitive information from VMs.
Example: In a cloud environment, an attacker could access databases or private business information, potentially stealing customer data or proprietary code.
Best Practices for Securing Hypervisors
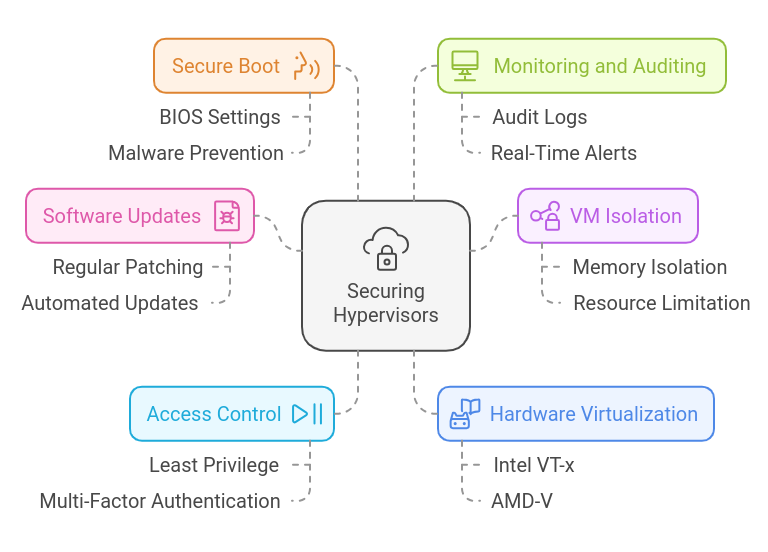
Here are practical steps to secure hypervisors:
Keep Software Updated
Hypervisor software should be regularly updated to fix security flaws. Promptly applying security patches can prevent attackers from exploiting vulnerabilities.
Example: When VMware releases a security patch for ESXi, install it as soon as possible to avoid potential exploits.
Automate updates where possible, but always test them in a safe environment before applying them.
Ensure Strong Isolation Between VMs
It’s important to isolate VMs to prevent one from affecting the others. This includes:
Memory isolation to prevent VMs from accessing each other’s memory.
CPU and resource isolation to ensure each VM has dedicated resources.
Setting limits on CPU or memory usage for each VM.
Example: Configuring VMware ESXi ensures that if one VM (say, VM-A) gets infected, it won't be able to access the memory or resources of another VM (VM-B).
Control Access to the Hypervisor
Restrict who can access and manage the hypervisor:
Use the principle of least privilege, granting only necessary permissions.
Implement Multi-Factor Authentication (MFA) to secure access.
Example: In Microsoft Hyper-V, only trusted administrators should have access to the system, and MFA should be enabled for logins.
Enable Hardware Virtualization Features
Modern processors have built-in features like Intel VT-x or AMD-V that enhance VM isolation and security.
Example: Enabling Intel VT-x in VMware ESXi's BIOS settings improves VM isolation and security.
Use Secure Boot
Secure boot ensures that only trusted software is loaded when the hypervisor starts, preventing unauthorized software from running.
Example: With Xen Hypervisor, enabling secure boot in the BIOS ensures no malicious software loads during startup.
Monitor and Audit Regularly
Keep track of activities on your hypervisor to detect unusual behavior:
Set up audit logs to track actions on the hypervisor.
Use real-time alerts to get notifications for suspicious activities.
Example: Tools like Splunk can help monitor your hypervisor. If there’s sudden unusual CPU usage or unauthorized access, you’ll receive an alert.
Advanced Security Measures for Hypervisors
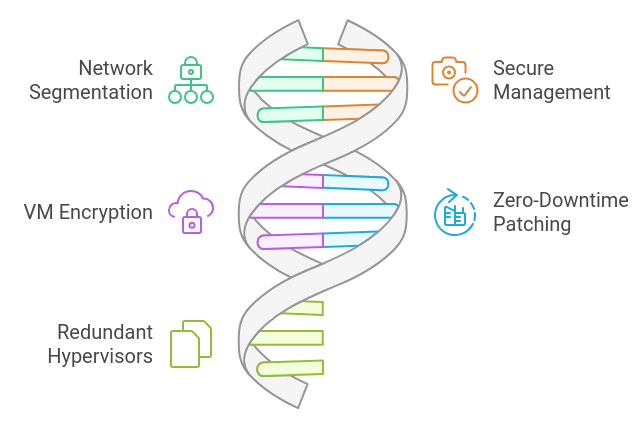
To further secure hypervisors, consider these advanced measures:
Network Segmentation
Divide the network into separate sections to reduce the impact of attacks.
Example: Put critical VMs on one network and less-sensitive VMs on another. This limits the potential damage if one section is attacked.
Secure Management Interfaces
Protect tools used to manage the hypervisor:
Restrict access to management tools with firewalls or VPNs.
Use Role-Based Access Control (RBAC) to assign access levels based on roles.
Example: Using VMware vCenter, ensure only authorized users can access the management console. A VPN can be used to restrict remote access.
Encrypt Virtual Machines
Encrypt data inside VMs to keep it secure, even if the hypervisor is compromised:
Encrypt data both at rest (when stored) and in transit (while being transferred).
Example: In Hyper-V, use BitLocker to encrypt VM data and SSL/TLS for encrypted communication between VMs.
Zero-Downtime Patching
Some hypervisors allow applying security patches without downtime, ensuring continuous operation.
Example: VMware vSphere allows security patches to be applied without needing to shut down running VMs.
Redundant Hypervisors
Have backup hypervisors to improve security and availability.
Example: Microsoft Hyper-V’s Hyper-V Replica allows you to replicate VMs to a backup hypervisor in case the primary one fails.
FAQ's
Conclusion: Securing Hypervisors for a Safer Cloud
Securing hypervisors is critical for maintaining the safety and reliability of cloud systems. Since hypervisors control VMs, which can store sensitive data, ensuring their security is essential to preventing breaches. By following best practices like regular software updates, isolating VMs, limiting access, and monitoring activities, you can significantly reduce the risks of attacks.
As technology continues to advance, adopting advanced security measures will further protect your cloud infrastructure and ensure a safer environment.
