Security in Cloud Computing: Risks, Responsibilities, and Controls
Cloud computing has reshaped how organizations build, deploy, and scale systems. But shifting infrastructure to the cloud doesn’t remove security risk, and it redistributes it. Data, access controls, and critical workloads now sit in environments where small missteps can expose large parts of the business.
According to IBM’s Cost of a Data Breach Report, the global average cost of a data breach reached $4.45 million, with incidents involving cloud environments among the most expensive to resolve. The takeaway is simple: cloud security failures are not theoretical, and their impact is measurable.
This article explains what security in cloud computing actually involves. You’ll learn the core risks organizations face, how responsibility is shared between cloud providers and customers, which controls meaningfully reduce risk, and how to evaluate whether your current cloud security posture is sufficient for long-term operations.
What cloud security covers
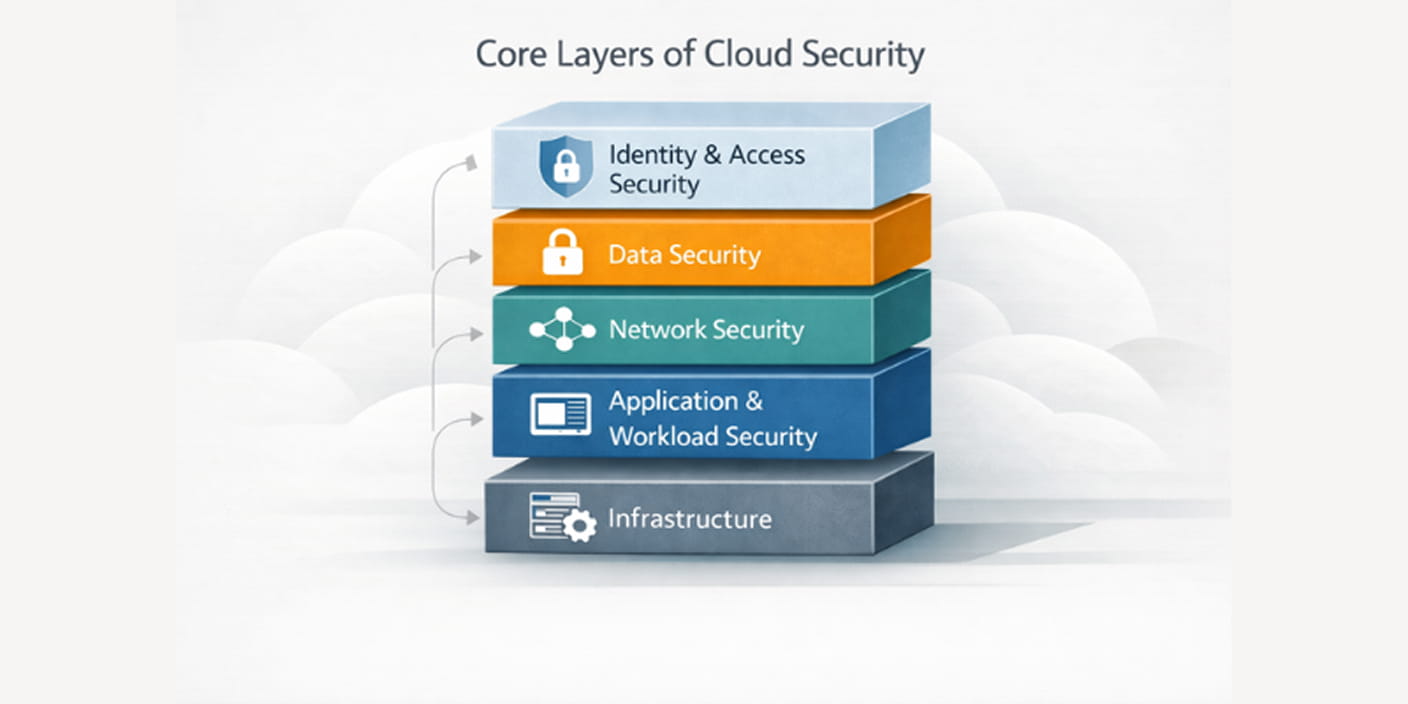
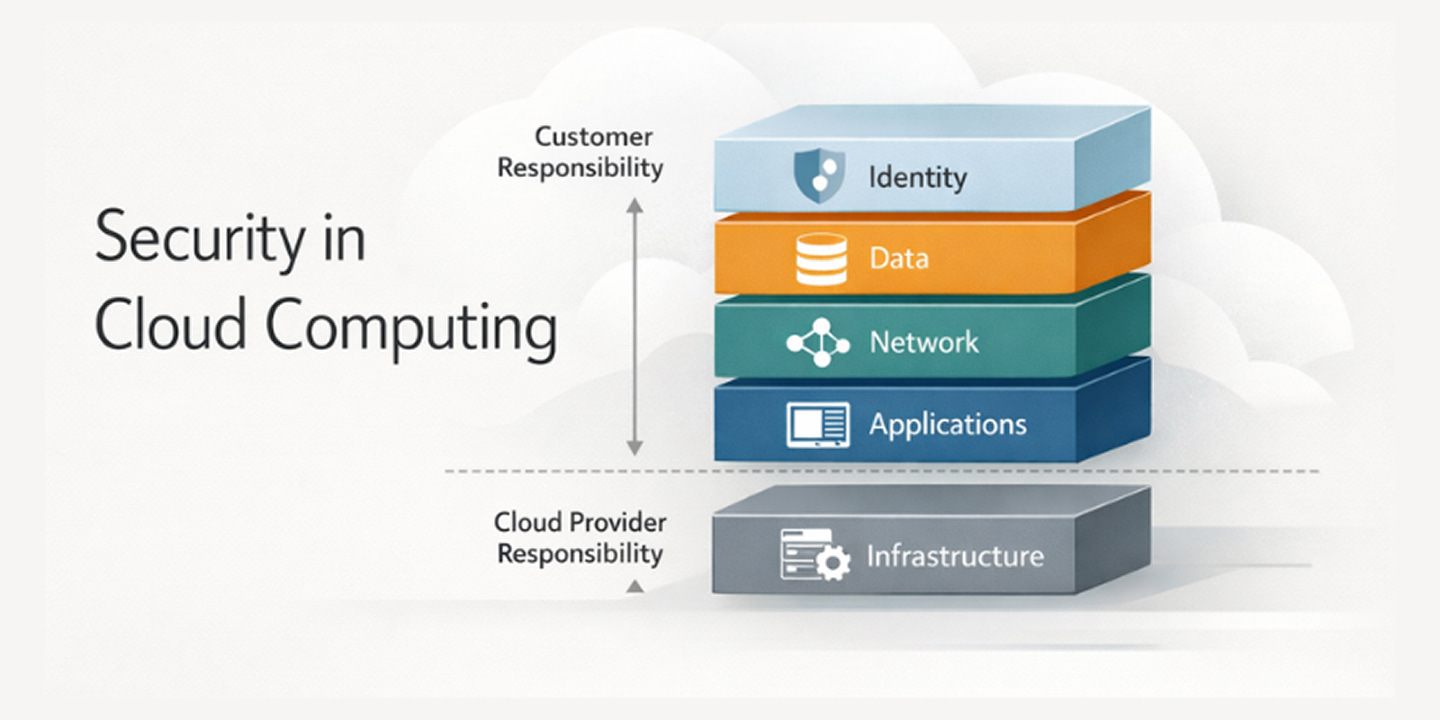
Cloud security often gets reduced to protecting data, but that narrow view is where many security gaps begin. In practice, cloud security spans multiple layers of the environment, each with its own risks, controls, and failure modes. Understanding these layers helps teams evaluate where responsibility sits and where controls are actually required.
It is also important to be clear about boundaries. Cloud security is not a single feature, and it is not handled entirely by the cloud provider. It is the combined outcome of how identity, data, networks, applications, and infrastructure are configured and operated.
Identity and access security
Identity is the control plane of the cloud. Most cloud environments are compromised not through sophisticated exploits, but through misused credentials, excessive permissions, or weak authentication practices. When identity controls fail, every other security layer becomes easier to bypass.
In practical terms, identity and access security focuses on:
Who can access cloud resources
What actions they are allowed to perform
How access is authenticated and reviewed over time
Poorly defined roles, long-lived credentials, and overly broad permissions are common causes of cloud security incidents. Strong identity controls reduce blast radius even when other defenses fail.
Data security
Data security covers how information is handled throughout its lifecycle in the cloud. This includes how data is stored, accessed, encrypted, backed up, and ultimately removed when no longer needed. While cloud providers secure the underlying storage systems, customers control how their data is exposed and used.
Key considerations include:
Encryption for data at rest and in transit
Access controls tied to identity policies
Backup and recovery planning
Data security failures are often the result of configuration decisions rather than platform weaknesses.
Network security
Cloud networks are software-defined, which makes them flexible but also easy to misconfigure. Network security determines how resources are exposed to the internet, how services communicate internally, and how traffic is filtered or restricted.
This layer focuses on limiting unnecessary exposure, enforcing segmentation, and reducing attack surfaces created by public endpoints or overly permissive routing.
Application and workload security
Applications and workloads introduce risk through insecure configurations, unpatched components, or exposed APIs. Even when infrastructure is sound, application-level weaknesses can undermine the entire environment.
This area covers how workloads are deployed, updated, isolated, and monitored, with particular attention to APIs and service-to-service communication.
Infrastructure security
Infrastructure security relates to how cloud resources are configured and monitored within the customer scope of control. While providers secure the physical data centers, customers are responsible for how compute, storage, and platform services are used.
Misconfigurations at this level often create systemic risk that affects multiple services at once.
Why cloud security is a business concern
Cloud security failures do not stay isolated within technical teams. When security controls break down in cloud environments, the impact surfaces quickly across revenue, operations, and customer trust. Because cloud platforms often support core business systems, even limited failures can have organization-wide consequences.
What differentiates cloud security risk is scale. Cloud environments centralize access, automation, and deployment, which means a single error can affect multiple systems at once. Small missteps often escalate faster than they would in traditional infrastructure.
Financial and operational impact
Cloud security incidents frequently result in measurable financial and operational disruption. Costs extend beyond technical remediation and often include downtime, delayed releases, and increased operational overhead while systems are stabilized.
From an operational standpoint, incidents force multiple teams to divert attention at the same time. Engineering, customer support, compliance, and leadership may all need to respond simultaneously, amplifying the overall business impact.
Reputational risk and customer trust
Security incidents in cloud environments are highly visible, particularly when customer-facing applications or sensitive data are involved. Even brief disruptions can raise concerns about reliability and data handling practices.
Reputational damage tends to persist longer than technical issues. Once trust is weakened, customers and partners may reassess risk, increasing scrutiny and lowering tolerance for future failures.
Scale and blast radius of failures
Cloud platforms are built to scale quickly, but that same design magnifies security mistakes. A single misconfigured policy or exposed service can impact multiple workloads or environments at once.
This expanded blast radius often results in:
Faster propagation of security failures
Increased difficulty in containment
Broader business impact from isolated errors
What would be a localized issue in on-prem environments can quickly become a widespread failure in the cloud.
Ownership and accountability for cloud risk
One of the most common contributors to cloud security failure is unclear ownership. Cloud risk typically spans security teams, IT operations, engineering, and leadership, but accountability is often fragmented across these groups.
When responsibilities are misaligned:
Security teams lack visibility or enforcement authority
Engineering teams prioritize speed over controls
Leadership underestimates exposure and downstream impact
Clear ownership and coordination across these roles is essential. Without it, cloud security failures are more likely to stem from organizational gaps than from technical limitations.
The shared responsibility model explained
Cloud security decisions often fail when teams assume responsibility is clearer than it actually is. The shared responsibility model defines how security duties are divided between the cloud provider and the customer, but it is frequently misunderstood. Without a clear view of these boundaries, organizations either overestimate what providers handle or underestimate their own obligations.
At a high level, cloud providers secure the underlying platform, while customers secure how cloud services are used, a distinction that becomes more critical in enterprise-grade cloud computing. The challenge lies in understanding where that line sits in practice, especially as service models change.
Provider and customer responsibilities
Cloud providers are responsible for securing the infrastructure that runs cloud services. This typically includes physical data centers, hardware, networking, and the core platform services that customers build on top of.
Customers are responsible for how their environments are configured and accessed. This includes identity controls, data protection, network exposure, application configuration, and monitoring. Most security incidents occur in this layer because configuration choices directly affect how resources are exposed.
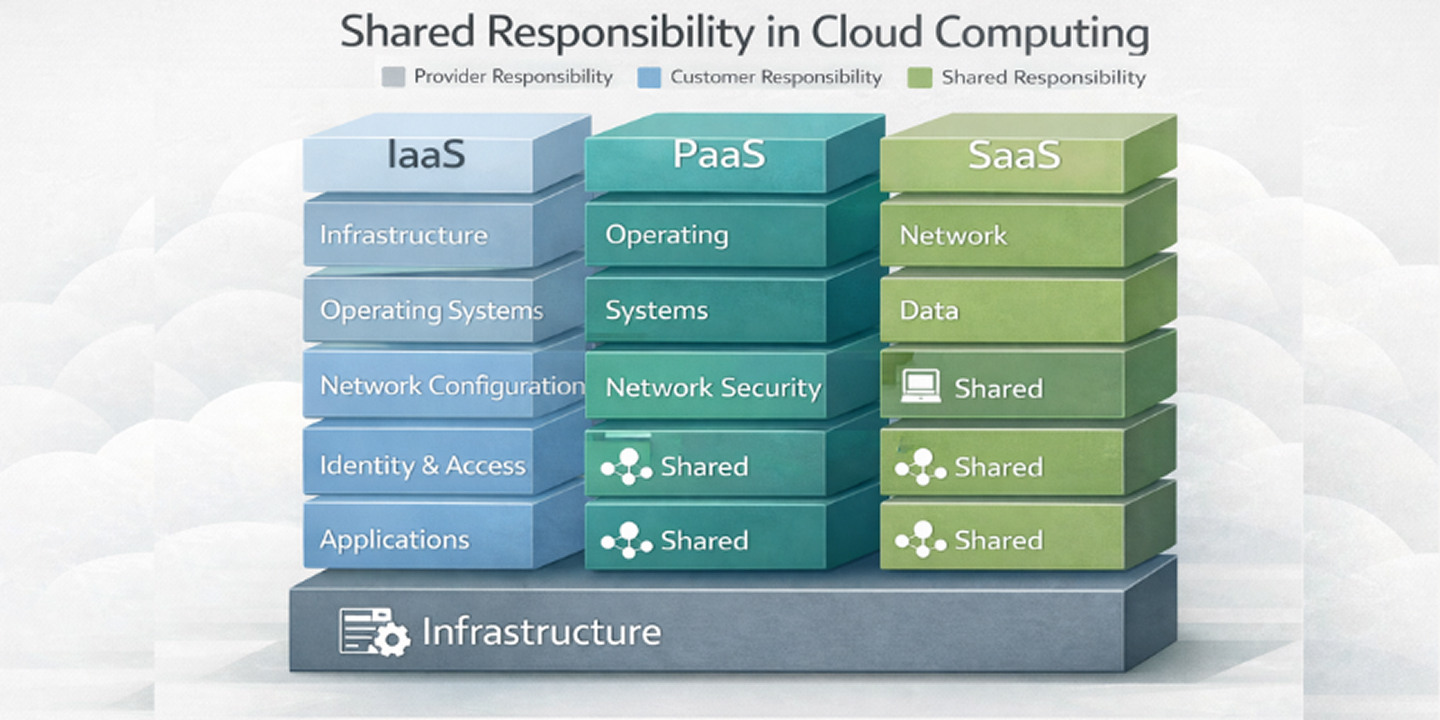
How does responsibility change across cloud service models?
Security responsibility in the cloud is not fixed. It shifts based on the service model an organization uses. Evaluating cloud risk without accounting for these differences often leads to incorrect assumptions about what is secured by the provider versus what must be managed internally.
While higher-level services reduce operational burden, they do not remove customer responsibility. Each model introduces different control boundaries that affect security ownership.
Infrastructure as a Service (IaaS)
In an IaaS model, the cloud provider secures the physical data centers, hardware, and foundational networking. Everything above that layer falls under customer control.
Customers are responsible for operating system security, network exposure, identity and access management, application configuration, and data protection. This model offers the most flexibility, but it also carries the highest risk if environments are poorly configured or insufficiently monitored.
Platform as a Service (PaaS)
With PaaS, the provider manages more of the underlying platform, including operating systems and runtime components. This reduces some operational responsibility but does not eliminate security obligations.
Customers remain responsible for application logic, access controls, data handling, and service-level configuration. Security failures in PaaS environments often stem from insecure application design or overly permissive access rather than platform weaknesses.
Software as a Service (SaaS)
In SaaS environments, the provider manages both the application and the infrastructure. This creates the impression that security is fully handled, which is rarely the case.
Customers are responsible for user access management, configuration settings, data usage, and compliance alignment. Many SaaS-related incidents result from mismanaged permissions or exposed data rather than flaws in the software itself.
As provider responsibility increases, customer responsibility narrows, but it never disappears.
The table below illustrates how security responsibility shifts across common cloud service models while highlighting areas that remain consistently customer-owned.
This breakdown helps explain why most cloud security incidents originate from customer-side decisions, even when higher-level services are used.
Commonly misunderstood responsibilities
Many cloud security failures occur in gray areas where responsibility feels shared but is not. Organizations often assume certain controls are handled automatically when they are not.
Common points of confusion include:
Access permissions that are overly broad by default
Public exposure of storage or services due to configuration choices
Logging and monitoring that exist but are not enabled or reviewed
Data retention and deletion policies that require customer action
These areas are frequently overlooked because they sit between platform capability and customer action.
Why misconfigurations are usually customer-side
Most cloud security incidents trace back to misconfigurations rather than platform vulnerabilities. Cloud providers supply secure defaults and guardrails, but customers control how those tools are applied.
Misconfigurations occur when environments grow quickly, changes are automated without review, or ownership is unclear. Without consistent governance and visibility, small configuration errors can persist unnoticed, increasing risk over time.
Understanding the shared responsibility model helps teams identify where security controls must be actively managed rather than assumed.
Core security risks in cloud computing
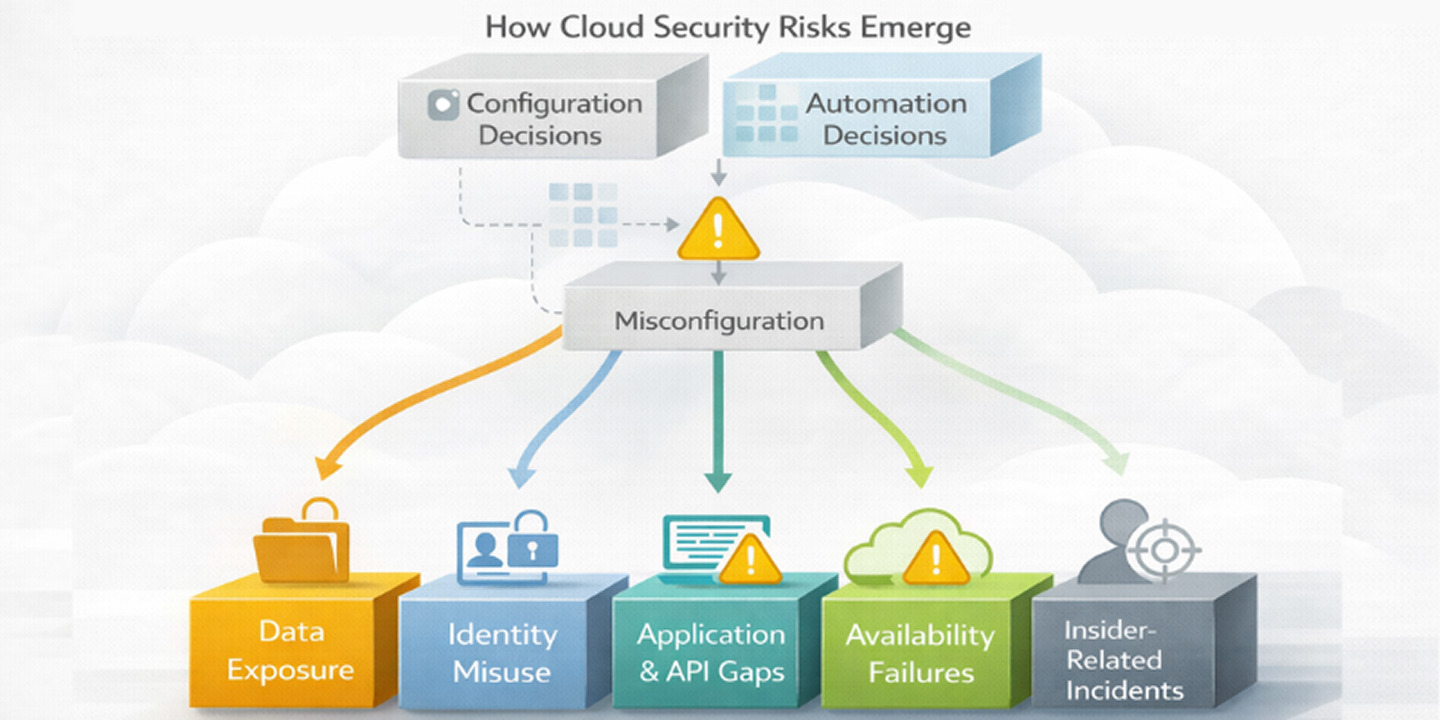
Understanding cloud security risk requires looking beyond isolated threat types. Most cloud incidents are not caused by advanced attacks but by routine decisions made during configuration, deployment, and access management. Grouping risks by how they occur provides a more practical view than disconnected “top 10” lists.
Across these categories, one pattern appears consistently: misconfiguration. Automation accelerates cloud operations, but it also amplifies mistakes when guardrails and reviews are missing, particularly in setups dependent on automated cloud security processes. Errors propagate faster, persist longer, and affect more systems at once.
Data exposure and data loss
Data exposure remains one of the most common cloud security risks. Sensitive information is often exposed through improperly configured storage services, weak access policies, or unintended data sharing between environments.
Typical drivers include:
Publicly accessible storage or services
Missing or inconsistent encryption settings
Incomplete backup and retention policies
These failures usually stem from configuration decisions rather than platform defects. Automation increases the likelihood that a single mistake is repeated across multiple workloads.
Identity and access misuse
Identity systems define who can access cloud resources and what actions they can perform. When access policies are overly permissive or poorly maintained, existing credentials become the attack path.
Access misuse often results from:
Excessive role permissions
Long-lived credentials or service accounts
Limited review of access changes over time
Automated provisioning accelerates these risks by assigning permissions faster than teams validate them.
Application and API security gaps
Applications and APIs expand the cloud attack surface as services become more distributed. Exposed endpoints, weak authentication, or missing controls can allow unauthorized access or abuse.
These risks are commonly introduced through configuration choices, such as unsecured endpoints or permissive API settings. Automation enables rapid deployment, but without consistent standards, it can replicate these gaps across environments.
Infrastructure and availability risks
Infrastructure risks affect service reliability and availability. While cloud providers supply foundational protections, customer configuration determines how resilient workloads actually are.
Availability issues often arise from:
Improper network exposure
Lack of segmentation between workloads
Inadequate capacity or failover planning
Automated scaling improves resilience when configured correctly, but it can also scale failures when underlying assumptions are flawed.
Insider and privilege-related threats
Insider risk in the cloud is frequently accidental rather than malicious. Employees or contractors may misuse privileges simply because access was never restricted or reviewed.
These risks increase when automation provisions access without sufficient oversight. Excessive permissions often persist longer than intended, raising the likelihood of both accidental exposure and intentional misuse.
Misconfiguration as a systemic risk
Misconfiguration ties all major cloud security risks together. Whether the issue involves data exposure, identity misuse, or service disruption, the root cause is often a configuration decision.
Automation magnifies this effect. When misconfigurations are embedded in templates or pipelines, they are consistently reproduced at scale. Treating configuration management as a security responsibility is essential to reducing cloud risk over time.
Visibility and monitoring challenges in the cloud
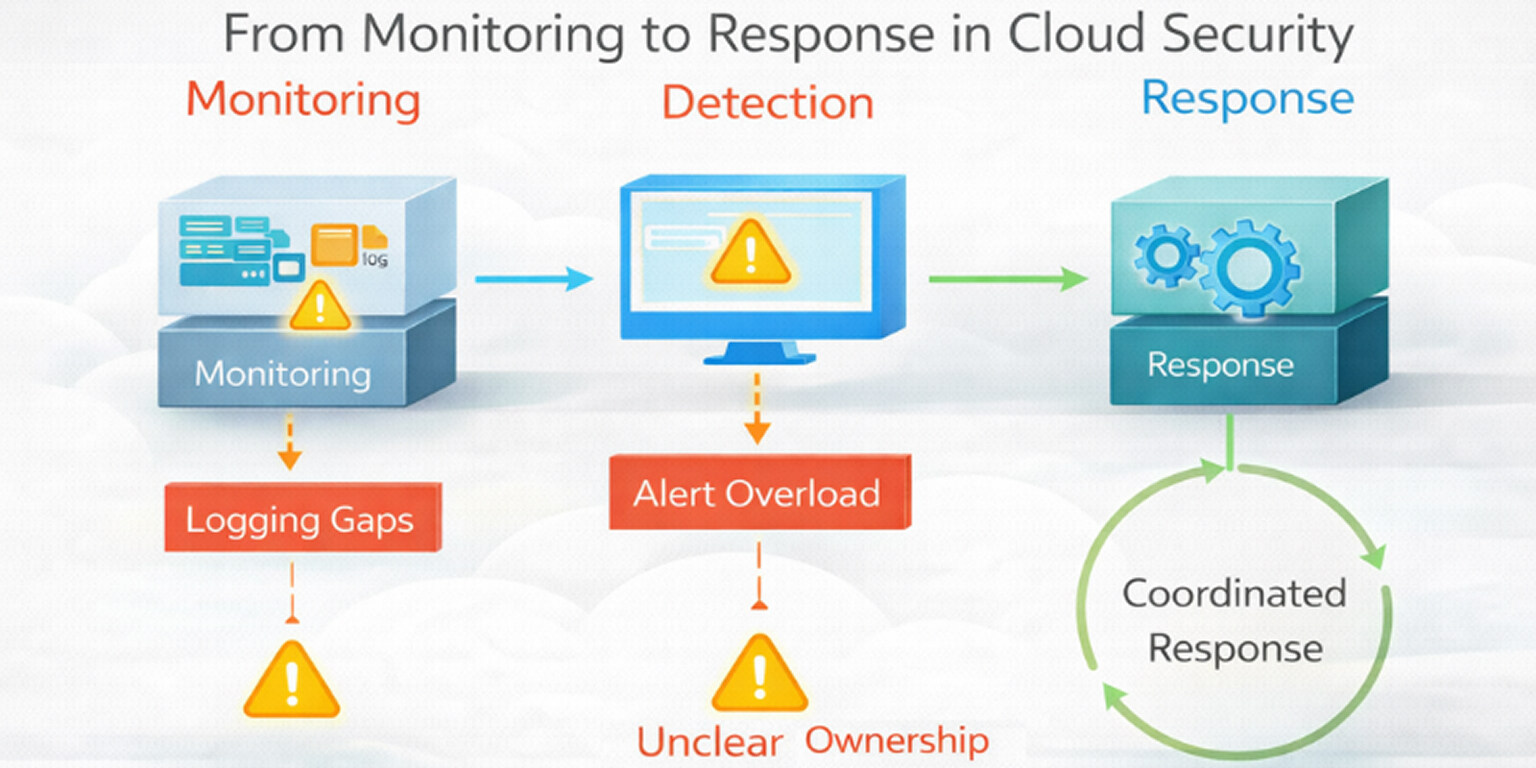
Visibility is one of the most persistent challenges in cloud security. Cloud environments change frequently, rely heavily on automation, and abstract much of the underlying infrastructure. As a result, teams often struggle to understand what is happening across accounts, services, and workloads at any given moment. Limited visibility increases the likelihood that security issues go unnoticed until their impact becomes difficult to contain.
Unlike traditional infrastructure, cloud platforms restrict direct access to underlying systems. While this improves platform safety, it also shifts how monitoring and investigation must be performed, requiring deliberate configuration and ongoing oversight.
Logging gaps and incomplete telemetry
Effective security monitoring depends on reliable logs. In cloud environments, logging is often available but not consistently enabled, retained, or reviewed. Critical activity may go unrecorded or be scattered across services, making investigation difficult.
Common causes of logging gaps include:
Logging disabled by default or left unconfigured
Inconsistent log retention policies across services
Limited visibility into managed services or third-party integrations
When logs are incomplete, teams lose historical context and struggle to determine how incidents occurred.
Alert fatigue and signal overload
Cloud platforms generate a high volume of alerts, many of which are low priority or poorly tuned. Over time, teams become desensitized to notifications, increasing the risk that meaningful warnings are ignored.
Alert fatigue often develops when monitoring focuses on activity volume rather than risk relevance. Without clear prioritization, security teams spend time reacting to noise instead of investigating genuine threats.
Monitoring versus detection versus response
Monitoring, detection, and response are often treated as interchangeable, but they serve different purposes. Monitoring collects activity data. Detection identifies patterns or behaviors that indicate potential risk. Response involves taking action to contain or remediate an issue.
Security programs frequently stall at monitoring. Logs and alerts exist, but no clear process defines how detected issues should be evaluated or resolved. Without response workflows, detection does not reduce risk, especially in environments without dedicated DevOps engineering teams to operationalize response.
Why alerts without response plans fail
Alerts only add value when they lead to action. In many cloud environments, alerts surface issues that no team owns or understands how to address.
Failures often occur when:
Alerts are not mapped to specific response steps
Ownership for response is unclear
Automation triggers alerts faster than teams can act
Without defined response plans, alerts become informational rather than protective. Effective cloud security requires connecting visibility, detection, and response into a coordinated process, similar to how security is integrated across modern DevSecOps phases.
Compliance, privacy, and regulatory risk
Compliance risk in the cloud is often underestimated because responsibility appears to shift to the provider. In practice, regulatory obligations follow the data and the business, not the infrastructure. Cloud platforms introduce flexibility and speed, but they also increase the number of ways compliance requirements can be unintentionally violated.
Privacy and regulatory exposure grow as cloud environments expand across regions, services, and teams. Without clear governance, organizations may meet platform standards while failing regulatory expectations.
Compliance complexity in cloud environments
Cloud environments make it easier to deploy services quickly, but that speed complicates compliance oversight. Data, access policies, and workloads change frequently, making it difficult to maintain consistent controls over time.
Compliance becomes harder when:
Services are deployed across multiple regions without clear data residency controls
Logging and audit trails are incomplete or inconsistently retained
Access permissions expand faster than reviews can keep up
These issues often arise from operational decisions rather than intentional noncompliance.
Responsibility boundaries and shared compliance
Cloud providers obtain certifications that demonstrate platform-level controls, but these certifications do not extend automatically to customer deployments. Provider responsibility typically covers the underlying infrastructure and service design.
Customers remain responsible for how services are configured, how data is handled, and how access is managed. Compliance failures frequently occur in this shared boundary, where assumptions about responsibility are unclear.
Common compliance failure patterns
Most cloud compliance violations follow predictable patterns rather than novel attack techniques. These failures tend to repeat across organizations and industries.
Common causes include:
Logging gaps that prevent audit reconstruction
Unclear data location or cross-region replication
Excessive access permissions without periodic review
Inconsistent enforcement of data retention and deletion policies
Each of these issues can place an organization out of compliance even when using compliant platforms.
Why certified providers do not guarantee compliance
A certified cloud provider demonstrates that its platform meets certain standards, not that every customer deployment does. Compliance depends on how services are used, configured, and governed.
Organizations that assume certification transfers automatically often overlook customer-side controls. Regulatory exposure emerges when compliance is treated as a platform feature rather than an operational responsibility.
Security controls that reduce cloud risk
Cloud security controls are often treated as individual safeguards, but their effectiveness depends on how they work together. In cloud environments, access, data movement, and configuration changes happen continuously. Controls applied in isolation can create blind spots rather than reduce risk.
What consistently reduces cloud risk is coordination. Identity, encryption, logging, and isolation reinforce one another when designed as a system instead of a checklist.
Identity and access controls
Identity and access controls determine who can interact with cloud resources and what actions they are permitted to perform. These controls sit at the center of most cloud security decisions.
Strong identity controls reduce risk by:
Limiting access to only what is required
Constraining administrative privileges
Enabling traceability of actions across services
Because nearly every security function relies on identity, weaknesses here undermine all other controls.
Encryption and data protection
Encryption protects data from unauthorized access, but it does not function independently. Its effectiveness depends on how encryption keys are managed and who is allowed to use them.
Encryption reduces risk most effectively when:
Access to keys is governed by identity policies
Key usage is logged and reviewed
Encryption is applied consistently across services
Without identity enforcement and logging, encrypted data can still be accessed inappropriately without detection.
Logging, monitoring, and auditability
Logging provides the visibility required to understand activity within cloud environments. Monitoring and audit trails support detection and investigation, but only when logs are complete and actionable.
Logging is most effective when it is
Enabled consistently across services
Linked to identity and access activity
Retained long enough to support investigations
Logs without context or ownership rarely lead to meaningful responses.
Network and workload isolation
Network segmentation and workload isolation limit how far incidents can spread. These controls reduce blast radius by restricting unnecessary communication between services.
Isolation works best when combined with identity and visibility. Without access enforcement or traffic insight, segmented environments can still be misused or bypassed.
Why controls fail when implemented in isolation
Cloud security controls frequently fail because they are deployed independently. Encryption without access governance, monitoring without response planning, or identity controls without visibility leave gaps that misconfigurations and misuse exploit.
Effective cloud security emerges when:
Identity governs access to data and services
Encryption protects data while logging records usage
- Isolation limits impact when failures occur
Controls reduce risk when they operate as a connected system rather than standalone safeguards, an approach aligned with architecture patterns for cloud-native systems.
Common cloud security mistakes teams make
Cloud security failures are rarely the result of unknown threats. Most incidents trace back to repeatable mistakes in how teams configure, operate, and govern cloud environments. Recognizing these patterns helps organizations evaluate risk honestly instead of assuming issues are isolated or exceptional.
These mistakes are usually not caused by missing tools. They emerge from decisions made under speed, unclear ownership, and weak operational discipline.
Misconfigurations treated as minor issues
Misconfiguration remains one of the most common causes of cloud security incidents. Storage exposure, permissive network rules, and overly broad access policies are often introduced during setup and never revisited.
Teams tend to underestimate these issues because they appear small or low risk at the time. In cloud environments, however, misconfigurations can:
Persist unnoticed for long periods
Be replicated automatically across environments
Expand impact as services scale
Automation increases efficiency, but it also multiplies configuration errors when guardrails are missing.
Over-trusting cloud providers
Cloud providers secure the underlying platform, but they do not secure customer configurations, access policies, or data usage. Teams sometimes assume that provider protections eliminate the need for customer-side controls.
This assumption leads to gaps in areas such as access governance, monitoring, and data handling. Provider security reduces certain infrastructure risks, but it does not prevent misconfiguration or misuse within customer environments.
Static security thinking in dynamic environments
Cloud environments change continuously. New services are deployed, permissions evolve, and architectures shift as teams iterate. Treating security as a one-time setup does not align with this operating model.
Static security approaches often result in outdated controls, unreviewed permissions, and growing exposure over time. Regular review and adjustment are required to keep security aligned with how the environment actually operates.
Lack of ownership and accountability
Cloud security typically spans security teams, IT operations, engineering, and leadership. When accountability is unclear, essential security tasks fall between roles.
Common symptoms include:
No single team responsible for access reviews
Inconsistent validation of logging and monitoring
Security issues discovered but not owned
Without clear ownership, risks accumulate quietly until they surface through incidents or audits.
Missing security review in cloud changes
Cloud changes are frequently introduced through automation, scripts, or deployment pipelines. When security review is not part of these workflows, risky changes reach production without oversight.
Process gaps often include:
Infrastructure changes without security validation
Permission updates without review
New services deployed without baseline controls
Many cloud security failures originate from process breakdowns rather than technical shortcomings. Embedding security review into cloud change workflows reduces repeatable risk.
When cloud security requires external expertise
Cloud security does not always require external help, but there are situations where internal teams reach practical limits. As cloud environments grow in complexity, certain risks become difficult to assess or address without independent perspective or specialized experience. Knowing when to bring in outside expertise helps organizations avoid both over-reliance and unnecessary exposure.
The goal of external support is not to replace internal ownership but to strengthen it. Effective use of external expertise complements existing teams rather than displacing them.
When external support becomes necessary
External expertise is most valuable when internal teams lack visibility, capacity, or specialized knowledge. This often occurs during periods of rapid growth, architectural change, or regulatory pressure.
Common indicators include:
Unclear understanding of current cloud security posture
Repeated findings from audits or internal reviews
Limited confidence in configuration consistency across environments
Regulatory or customer requirements that exceed internal experience
These signals suggest the need for independent assessment rather than ongoing outsourcing.
Assessments versus managed services
Not all external security support serves the same purpose. Understanding the distinction helps teams choose the right level of involvement.
Security assessments focus on evaluating current risk. They typically include configuration reviews, access analysis, and control effectiveness evaluation. Assessments provide clarity on gaps and priorities while leaving remediation decisions with the internal team.
Managed security services provide ongoing operational support. These services may include monitoring, response assistance, or control management. They are appropriate when internal capacity is limited, but they require clear boundaries to avoid dependency.
What should not be outsourced
Certain responsibilities should remain internal, even when external expertise is involved. Outsourcing these areas often weakens long-term security posture.
Responsibilities best kept in-house include:
Ownership of risk decisions and priorities
Approval of access and configuration changes
Accountability for compliance and governance
External experts can advise and assist, but internal teams must retain control over decisions that affect business risk.
Avoiding over-reliance on third parties
A common concern is losing control by engaging external security providers. This risk increases when roles and expectations are not clearly defined.
External expertise is most effective when it supports internal processes, not when it replaces them. Clear ownership, defined scope, and retained decision authority ensure that external support strengthens cloud security rather than diluting accountability.
Evaluating your cloud security posture
Evaluating cloud security posture is less about passing a checklist and more about understanding risk in context. Many organizations struggle because assessments focus on whether controls exist, not whether they meaningfully reduce exposure. A practical evaluation helps decision-makers determine where risk is acceptable, where it is not, and what to address first.
An effective assessment mindset emphasizes clarity over completeness. The goal is to make informed decisions based on actual exposure rather than to achieve an idealized security state.
Assessment as a risk-based exercise
Cloud security posture should be evaluated through the lens of risk, not feature coverage. Controls matter only to the extent that they reduce the likelihood or impact of failure.
A risk-based assessment asks:
Which systems and data matter most to the business
How those assets could realistically be exposed
What failures would cause the most operational or financial harm
This framing keeps assessments focused on outcomes rather than control inventories.
Prioritization over maturity theater
Many organizations fall into maturity theater, where progress is measured by how many controls are implemented rather than by how much risk is reduced. This often creates complex security programs that appear comprehensive but leave critical weaknesses unresolved.
Prioritization means making deliberate trade-offs. Addressing a small number of high-impact risks often provides more protection than spreading effort evenly across lower-risk areas.
Why perfection is unrealistic in the cloud
Cloud environments are designed to change continuously. New services are introduced, configurations evolve, and access patterns shift as teams work. Expecting a permanently complete or static security posture does not align with how cloud systems operate.
Effective security accepts that gaps will exist and focuses on reducing exposure over time rather than eliminating every possible weakness.
Turning assessment into action
An evaluation only matters if it informs decisions. Assessment results should translate into clear ownership, prioritized remediation, and an understanding of residual risk, which often requires experienced cloud infrastructure developers to execute effectively.
Effective assessments lead to:
Clear identification of the most significant risks
Agreement on which issues require action versus acceptance
Ongoing reassessment as environments change
When evaluation drives action instead of documentation, cloud security posture improves in practical, measurable ways.
Key takeaways for long-term cloud security
Long-term cloud security is shaped by how consistently decisions are made, not by one-time implementations. Cloud platforms, services, and usage patterns evolve continuously, and security outcomes reflect how well responsibility, visibility, and risk management adapt over time.
Rather than focusing on completeness, effective cloud security emphasizes clarity. Organizations that understand where responsibility lies and how risk changes are better positioned to sustain security as environments grow.
Responsibility must be explicit
Cloud security is shared, but accountability cannot be vague. When ownership is unclear, access reviews are skipped, logging degrades, and configuration drift goes unchallenged. Clear responsibility ensures that security tasks are not treated as optional or assumed to belong to someone else.
Strong programs define who owns identity policies, who approves infrastructure changes, and who responds to incidents. This clarity prevents gaps created by handoffs between security, engineering, and operations teams.
Misconfiguration is the dominant risk driver
Most cloud incidents trace back to configuration decisions, not platform failures. Storage exposure, excessive permissions, and insecure defaults are common because cloud environments prioritize flexibility and speed.
Automation magnifies this effect. When insecure patterns are embedded into templates or pipelines, the same mistake is reproduced across environments. Treating configuration management as a security discipline is one of the most reliable ways to reduce long-term risk.
Controls must reinforce each other
Individual safeguards provide limited protection in isolation. Identity controls without logging create blind spots. Encryption without access governance still allows misuse. Network isolation without visibility delays detection.
Effective cloud security emerges when controls operate as a system. Identity limits access, encryption protects data, logging records activity, and isolation contains failures. Weakness in any layer reduces the value of the rest.
Visibility without response is insufficient
Monitoring and alerts do not reduce risk on their own. They only become protective when issues trigger clear investigation and remediation steps.
Organizations that invest heavily in telemetry but lack ownership or response workflows often detect incidents without being able to contain them quickly. Security maturity depends as much on operational readiness as on technical instrumentation.
Compliance depends on usage, not certification
Provider certifications demonstrate platform controls, not customer behavior. Regulatory exposure is driven by how data is stored, who can access it, how activity is logged, and whether retention policies are enforced.
Treating compliance as a deployment responsibility rather than a vendor attribute helps prevent audit failures and regulatory surprises.
Conclusion
Cloud security is not defined by where infrastructure runs but by how responsibility, configuration, and risk are managed over time. Most cloud security failures stem from routine decisions made at scale, not from sophisticated attacks or platform weaknesses.
Organizations that secure cloud environments effectively focus on clarity rather than complexity. They understand what the cloud provider secures, where customer responsibility begins, and how misconfigurations and process gaps introduce risk.
Long-term cloud security comes from treating security as an ongoing operational discipline. Clear ownership, coordinated controls, meaningful visibility, and risk-based prioritization allow teams to reduce exposure as cloud usage grows, without chasing unrealistic perfection.
