Best DevSecOps Tools for Application Security

DevSecOps helps teams identify and repair vulnerabilities early in the CI/CD pipeline by implementing security directly into the development and operations workflow.
Using the appropriate tools is crucial to maintaining speed and security as cloud platforms like AWS become increasingly important for application deployment. This blog showcases dependable DevSecOps solutions that protect infrastructure and apps without interfering with your development process.
For a deeper look into planning and scaling secure development workflows, start here.
Code is being released by development teams more quickly than ever before, with 71% of organizations doing weekly updates, but if not controlled carefully, this speed could reveal shortcomings in security.
DevSecOps bridges this gap by embedding security into the CI/CD pipeline. Early adopters report 40% faster delivery and 80% fewer vulnerabilities, showing that security and speed can go hand in hand (Source).
In 2025, over 80% of organizations now use Infrastructure as Code (IaC) tools like Terraform or CloudFormation.
Best DevSecOps Tools for Application Security

1. Snyk
Snyk is a developer-first security platform that detects and addresses vulnerabilities in Infrastructure as Code (IaC), container images, and open-source dependencies. It is a good option for DevSecOps teams using shift-left security since it fits in well with Git-based processes and provides real-time security feedback without affecting development velocity.
Key Features
- Real-time vulnerability scanning of dependencies and containers
- Inline fix suggestions directly within IDEs and Git workflows
- Native integrations with GitHub, GitLab, Bitbucket, Jenkins, and CircleCI
- Covers multiple security domains: SCA, container security, and IaC scanning
Case: Skyscanner
Skyscanner, a global travel search engine, adopted Snyk to manage the security of its fast-growing microservices architecture. The engineering team integrated Snyk into their CI/CD pipeline, enabling automated scans of dependencies and Docker containers.
Within months, they reduced critical vulnerabilities across key services by over 70% and maintained fast release cycles without adding friction to the developer experience.
This shift empowered Skyscanner’s developers to take ownership of security earlier in the lifecycle, transforming security from a bottleneck into a shared responsibility.
2. Aqua Security
Aqua Security is a leading cloud-native application protection platform (CNAPP) built to secure containers, Kubernetes environments, serverless workloads, and infrastructure across the software lifecycle. It offers deep visibility and runtime protection without compromising the agility of DevOps teams. Aqua is purpose-built for securing modern, distributed applications at scale.
Key Features
- Detects vulnerabilities and misconfigurations in container images and Kubernetes deployments before they reach production.
- Monitors runtime environments to block unauthorized activity, privilege escalation, and container drift.
- Scans Terraform, CloudFormation, and Helm files to catch risky configurations before deployment.
- Applies role-based access controls to enforce least-privilege policies across users, workloads, and cloud environments.
Case Study: Nasdaq
Nasdaq, the global financial services company, adopted Aqua Security to secure its containerized workloads across Kubernetes clusters. Facing regulatory requirements and operational complexity, Nasdaq leveraged Aqua’s runtime defense and policy enforcement features.
As a result, they improved their runtime visibility and proactively blocked malicious behaviors, ensuring continuous compliance and securing sensitive financial data without slowing innovation.
3. SonarQube
SonarQube is a widely adopted static application security testing (SAST) and code quality tool that helps developers detect bugs, code smells, and security vulnerabilities early in the software development lifecycle.
Designed to integrate with CI/CD pipelines, SonarQube enforces clean code practices and promotes security standards across more than 25 programming languages. It’s particularly valuable for teams seeking to embed security into their coding practices without slowing down delivery.
Key Features
- SonarQube scans for security issues, bugs, and code smells across a wide range of languages, including Java, JavaScript, Python, and C#.
- It integrates smoothly with CI/CD pipelines like Jenkins, GitLab, and Azure DevOps to automate code analysis during builds.
- Customizable quality gates can be set to block deployments that contain critical vulnerabilities or fail to meet coding standards.
- With SonarLint, developers receive real-time feedback directly within their IDEs, promoting secure and maintainable code from the start.
Case Study: Deutsche Bank
Deutsche Bank integrated SonarQube across its global development teams to ensure consistent code quality and security standards.
By embedding SonarQube into its CI/CD pipelines, the bank was able to reduce critical code vulnerabilities by over 60% and enforce internal coding standards across diverse teams.
The real-time feedback loop empowered developers to resolve issues during development rather than post-deployment, improving both code maintainability and security posture.
4. Checkmarx
Checkmarx is a Static Application Security Testing (SAST) tool built to identify vulnerabilities in source code early in development. It integrates with CI/CD pipelines and supports over 25 programming languages, making it ideal for secure, enterprise-scale workflows. Its customization options and developer-focused features help reduce risk without slowing down delivery.
Key Features
- Checkmarx supports static code analysis (SAST) for over 25 programming languages.
- It integrates smoothly with CI/CD tools like Jenkins, GitHub Actions, and GitLab.
- Custom security rules can be created using its built-in query language, CxQL.
- The platform combines SAST, SCA, and IaC scanning in a single unified interface.
Case Study: Siemens
Siemens, a global industrial and tech powerhouse, adopted Checkmarx to improve secure coding practices across multiple development teams. By integrating Checkmarx into their CI/CD pipeline, Siemens enabled automated, real-time security scans across hundreds of applications.
This shift empowered developers to fix vulnerabilities earlier and reduced their average time-to-remediate critical flaws by over 60%. The result was stronger collaboration between security and engineering teams, without slowing down innovation.
5. HashiCorp Vault
HashiCorp Vault is a secrets management tool that securely stores and manages sensitive data like API keys, tokens, and certificates. It supports dynamic secrets, access control, and encryption, making it essential for protecting infrastructure in modern DevSecOps workflows.
Key Features
- Issue secrets on-demand (e.g., database credentials) that automatically expire, minimizing exposure risk.
- Enables API-based encryption for data at rest and in transit without modifying applications.
- Enforces access policies using integrations like AWS IAM, Kubernetes, LDAP, or GitHub.
- Logs every request for auditing, compliance, and security visibility.
Case Study: Adobe
Adobe, known for its creative software and cloud platforms, integrated HashiCorp Vault to manage secrets across its multi-cloud environments.
With thousands of microservices and services communicating internally, Adobe used Vault to eliminate hardcoded secrets, adopt dynamic secret generation, and implement fine-grained access control across teams.
As a result, Adobe significantly reduced its exposure to credential leaks and improved compliance with internal audit and regulatory requirements, without slowing down development velocity or requiring major architectural rewrites.
6. OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is a free, open-source DAST tool used to find vulnerabilities in running web applications. Known for its automated and manual testing capabilities, ZAP is a go-to choice for detecting common threats, such as XSS and SQL injection, making it ideal for integrating security into CI/CD pipelines during testing or staging phases.
Key Features
- It automatically detects common web application vulnerabilities through both passive and active scanning methods.
- The tool allows users to inspect and modify traffic between the client and server during testing.
- ZAP supports custom scripting, enabling tailored scans and advanced testing logic.
- It integrates smoothly with CI/CD tools like Jenkins and GitHub Actions for continuous security testing.
Case Study: Mozilla’s Integration of OWASP ZAP
Mozilla uses OWASP ZAP as part of its internal security testing process for Firefox web services. By integrating ZAP into their automated CI/CD pipelines, they’ve been able to run security scans regularly against staging environments, detecting issues early without delaying release cycles. ZAP’s extensibility also allowed Mozilla’s team to write custom scripts for more targeted scans, reinforcing their DevSecOps strategy while keeping costs at zero.
7. WhiteSource
WhiteSource, now known as Mend, is a Software Composition Analysis (SCA) tool that helps secure open-source components. It automates vulnerability detection, license compliance, and remediation across CI/CD pipelines, making it ideal for teams relying on third-party libraries.
Key Features
- Real-time Vulnerability Scanning of open-source packages across multiple repositories
- License Risk Management to ensure legal compliance with third-party components
- Automated Remediation via pull requests and patch suggestions
- Custom Security Policies to enforce governance across teams and projects
Case Study: Hillrom (a Baxter company)
Hillrom, a global medical technology provider, implemented WhiteSource to enhance security and compliance across its product development pipeline. By integrating it into their Jenkins CI/CD process, they automated vulnerability scans and license checks across thousands of open-source components.
Within a few months, Hillrom reduced manual auditing time by 60%, improved response to newly discovered CVEs, and achieved consistent license compliance across all business units. This automation allowed developers to focus on building features while maintaining strong security oversight.
8. Netsparker
Netsparker is a dynamic application security testing (DAST) tool built to automatically detect and verify vulnerabilities in web applications and APIs. It uses a unique proof-based scanning technology to confirm the existence of flaws like SQL injection and XSS, reducing false positives significantly. Designed for security teams and DevOps engineers alike, Netsparker integrates smoothly into CI/CD pipelines, allowing for continuous testing without disrupting development speed.
Key Features
- Netsparker automatically confirms vulnerabilities by safely exploiting them, significantly reducing the number of false positives.
- It integrates smoothly with CI/CD tools like Jenkins, Azure DevOps, and GitHub Actions to enable automated security scans during development workflows.
- Users can customize scan configurations and vulnerability detection rules to align with their organization’s internal security policies.
- The platform also supports scanning of RESTful APIs and complex authentication processes, making it ideal for modern web applications and services.
Case Study: TÜV Rheinland
TÜV Rheinland, a global leader in testing and certification, integrated Netsparker into their development lifecycle to enhance web application security across multiple departments.
Using Netsparker’s automated scanning and proof-based detection, the team reduced false positives by over 80%, freeing up resources to focus on confirmed issues.
The tool’s integration into Jenkins enabled continuous security checks for every deployment, aligning with their DevSecOps strategy without slowing down delivery timelines.
9. Veracode
Veracode is a cloud-based application security platform that offers SAST, DAST, SCA, and manual testing in one solution. Built with DevSecOps in mind, it helps teams detect and fix vulnerabilities early, without slowing down software delivery.
Key Features
- Unified platform for SAST, DAST, SCA, and manual testing
- Developer-friendly remediation guidance with contextual fix suggestions
- Integrations with popular CI/CD tools like Jenkins, Azure DevOps, and GitHub Actions
- Policy-driven compliance reporting for SOC 2, ISO, HIPAA, and more
Case Study: Mimecast
Mimecast, a global cybersecurity company, turned to Veracode to strengthen the security of its rapidly scaling software products. By integrating Veracode's SAST and SCA tools into their CI/CD process, Mimecast reduced the average time to remediate vulnerabilities by 60%. Additionally, their engineering teams gained increased visibility into risk exposure, allowing for faster, more secure deployments across multiple environments. Veracode’s policy automation also helped them stay audit-ready for regulatory compliance with minimal manual intervention.
How to choose the right DevSecOps tools
Choosing the right DevSecOps tools isn’t just about picking what’s popular; it’s about finding what fits your development workflow, risk profile, and scale. Here are the key factors to guide your decision:
1. Integration with Your CI/CD Pipeline
The tool must plug smoothly into your existing toolchain, whether it’s GitHub Actions, GitLab CI, CircleCI, or Jenkins. Tight integration ensures that security scans run automatically during builds without slowing down releases.
2. Coverage Across Security Domains
Opt for tools that address multiple threat vectors, code vulnerabilities (SAST), runtime flaws (DAST), container risks, misconfigured infrastructure (IaC), and leaked secrets. A well-rounded toolset helps you avoid security blind spots.
3. Automation & Smart Remediation
Look for tools that don’t just detect issues but help fix them via inline suggestions, auto-patches, or pull request integrations. This reduces manual overhead and encourages dev teams to resolve problems quickly.
4. Developer-Friendliness
Tools should work with developers, not against them. IDE plugins, easy-to-read reports, and low-friction onboarding matter. Dev-first tools lead to better adoption.
5. Open Source vs Commercial
Open-source tools offer flexibility and community support, but enterprise-grade solutions often include better dashboards, compliance reporting, and support.
6. Growth Readiness & Alert Fatigue
A tool that overwhelms teams with low-priority alerts does more harm than good. Prioritize those with smart filtering, prioritization, and role-based controls.
Start by identifying the gaps in your current workflow, then layer tools based on maturity, budget, and team experience.
Categories of DevSecOps tools
DevSecOps tools span multiple stages of the software development lifecycle, each addressing specific areas of application security. For a structured implementation, it’s helpful to break these tools into categories based on their core functionality.
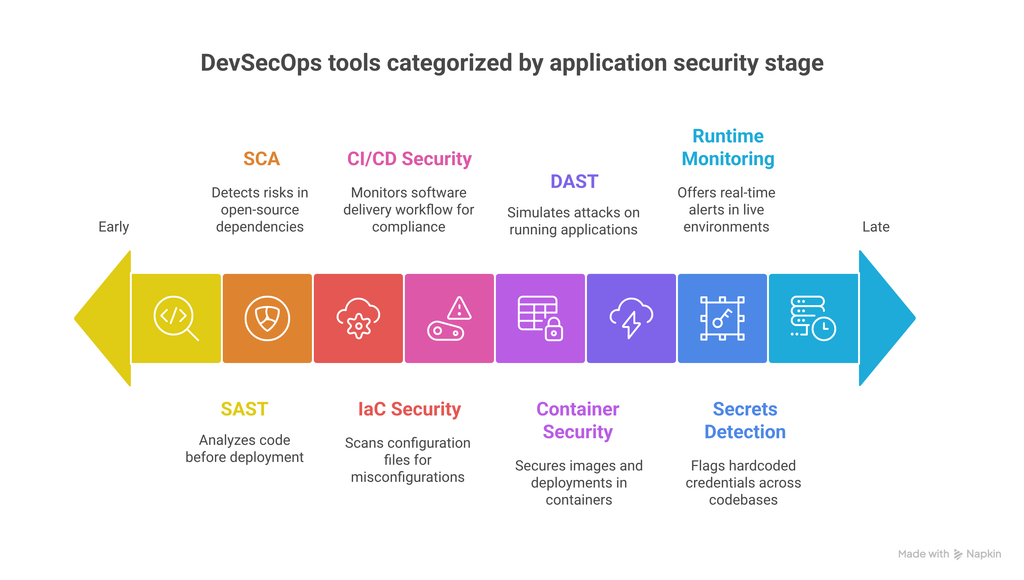
1. Static Application Security Testing (SAST)
SAST tools scan source code or binaries early in development to catch vulnerabilities like XSS or SQL injection. They help developers fix issues before the code is deployed. Ideal for shift-left security and continuous integration workflows.
2. Dynamic Application Security Testing (DAST)
DAST tools simulate real-world attacks to evaluate live apps. They identify runtime problems such as unprotected endpoints or broken authentication. Excellent for identifying defects that code-level searches overlook.
3. Software Composition Analysis (SCA)
SCA tools look for known vulnerabilities and licensing issues in open-source dependencies. They offer safer alternatives and assist in overseeing third-party packages. crucial for modern apps that rely on third-party libraries.
4. Container & Kubernetes Security
These tools check orchestrator settings and container images for vulnerabilities and misconfigurations. They keep an eye out for inconsistencies and enforce runtime policies. essential for safeguarding microservices and cloud-native architectures.
5. Infrastructure as Code (IaC) Security
Before deployment, IaC security tools examine Terraform or CloudFormation files to identify potentially dangerous configurations. They stop problems like unencrypted storage and open ports. helps guarantee safe infrastructure from the beginning.
6. Secrets Detection
Tools for detecting secrets alert developers about hardcoded keys, tokens, or passwords in source code. They minimize the possibility of credential leaks when commits are being made. Vital for protecting sensitive information in version control.
7. CI/CD Pipeline Security
These tools enforce security steps across your CI/CD workflow, like scans, approvals, and artifact signing. They help ensure secure, repeatable deployments without manual gaps.
8. Runtime Threat Detection & Monitoring
Runtime tools monitor production environments for suspicious activity and policy violations. They provide real-time alerts and support zero-day threat detection. Key for securing applications post-deployment.
Common mistakes to avoid in DevSecOps adoption
Integrating DevSecOps into the development lifecycle requires more than deploying a set of tools. Organizations often misstep in ways that reduce the effectiveness of their security posture. Avoiding the following pitfalls can lead to more consistent and secure application development:
Overreliance on tools without a security culture
- Relying solely on tools without investing in developer training or secure coding practices can result in missed vulnerabilities. Tools support security; they don’t replace it.
Tool Sprawl and Alert Fatigue
- Adopting too many tools without clear ownership or integration often leads to duplicate alerts, low-priority noise, and team fatigue. Focus on quality over quantity.
Delayed security integration
- Introducing security scans late in the pipeline reduces their value. Security should be embedded from the first line of code, left-shifted into the development workflow.
Misalignment with developer workflows
- Security solutions that interrupt or slow down development cycles are often bypassed. Tools must integrate smoothly with IDEs, CI/CD, and version control systems.
Lack of accountability
- Without clear roles and responsibilities for addressing vulnerabilities, issues remain unresolved. Define ownership and ensure response plans are in place.
By recognizing and addressing these challenges early, teams can build a more resilient, developer-friendly, and effective DevSecOps strategy.
DevSecOps Tools Comparison Table
Conclusion
Choosing the right DevSecOps tools is more than a technical decision; it’s a strategic one that shapes how fast and securely your team can deliver software. Selecting the best DevSecOps technologies is a strategic choice that affects how quickly and securely your team can produce software. It's not just a technical one. From protecting secrets and keeping an eye on runtime risks to scanning code and containers, the tools presented provide comprehensive coverage across important security domains.
However, even the best tools fall short without the right implementation strategy. Success lies in aligning security with development workflows, empowering teams, and avoiding common pitfalls like alert fatigue or tool overload.
To explore the essential stages and foundational steps of a successful DevSecOps journey, from assessment to full integration, check them out here.